Sunday, July 16, 2017
Beginners Guide To Armitage And How To Use It In Kali Linux
Beginners Guide To Armitage And How To Use It In Kali Linux

Armitage is a graphical user interface for the Metasploit Framework. At first glance, it may seem that Armitage is just a pretty front-end on top of Metasploit. That’s not quite true. Armitage is a scriptable red team collaboration tool. It has a server component to allow a team of hackers to share their accesses to compromised hosts. This is essentially a GUI way of using metasploit/meterpreter I hope you find it useful as many people like to use GUI rather than cmd line.
Lets get started,
First navigate to Applications > Kali Linux > System Services > Metasploit > community / pro start ...... this will start the server/database

Then type armitage in the terminal window and accept the default values:
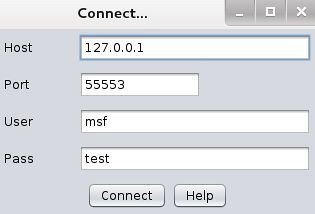
You will probably get a popup asking to start metasploit, click yes
you should now see the following:

Dont worry about the connection refused it just takes a while to load.
Now armitage will boot up if it asks you for the attack computer IP enter your IP Address.
Navigate to the Hosts tab > Nmap Scan > Quick Scan (OS Detect)

From here armitage will scan a range or a sigle IP Address of your choice then present it in theblack window. Right click the target and click Scan
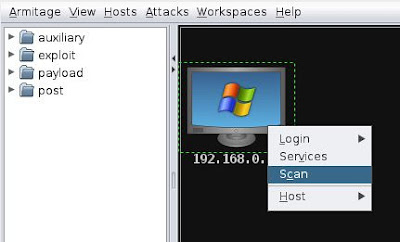
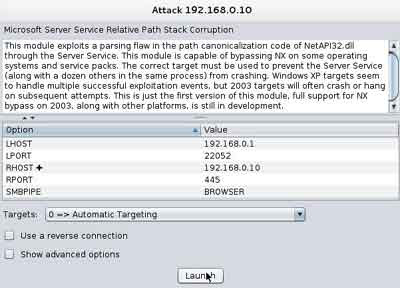
When the scan is complete expand the exploit > windows > smb and double click the ms08_67_netapi

This will bring up an attack confirmation window check the details and click launch
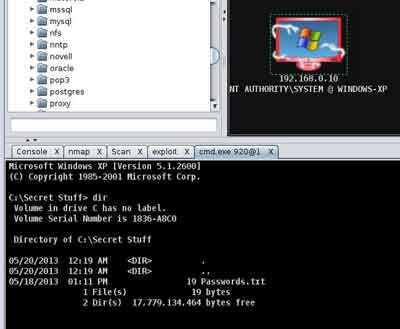
Confirmation of a successful exploit will look like this:

You can now right click the target and perform multiple commands

here is an example of the Interact "remote command shell"
If you have any doubts or suggestions please comment below, Thank you.
Available link for download